An often overseen action is to lock down Internet Information Services. You can increases security of SSL connections to your server by disabling insecure SSL2 and SSL3 and all insecure and weak ciphers that a browser may fall-back, too. I recently found a great PowerShell script, which can help implement the current best practices for IIS in a quick way.
This PowerShell script setups your Microsoft Internet Information Server 7.5/8.0/8.5/10 (IIS) on Windows 2008R2/2012/2012R2/2016 to support TLS 1.1 and TLS 1.2 protocol with Forward secrecy.
It is also a way to be compliant with Security Audit, that scan you web services.
The script enables or disables the following:
- Disable Multi-Protocol Unified Hello
- Disable PCT 1.0
- Disable SSL 2.0 (PCI Compliance)
- Disable SSL 3.0 (PCI Compliance) and enable “Poodle” protection
- Add and Enable TLS 1.0 for client and server SCHANNEL communications
- Add and Enable TLS 1.1 for client and server SCHANNEL communications
- Add and Enable TLS 1.2 for client and server SCHANNEL communications
- Disable insecure/weak ciphers:
- DES 56/56
- RC2 128/128
- RC2 40/128
- RC2 56/128
- RC4 40/128
- RC4 56/128
- RC4 64/128
- RC4 128/128
- Enable new secure ciphers:
- AES 128/128
- AES 256/256
- Triple DES 168
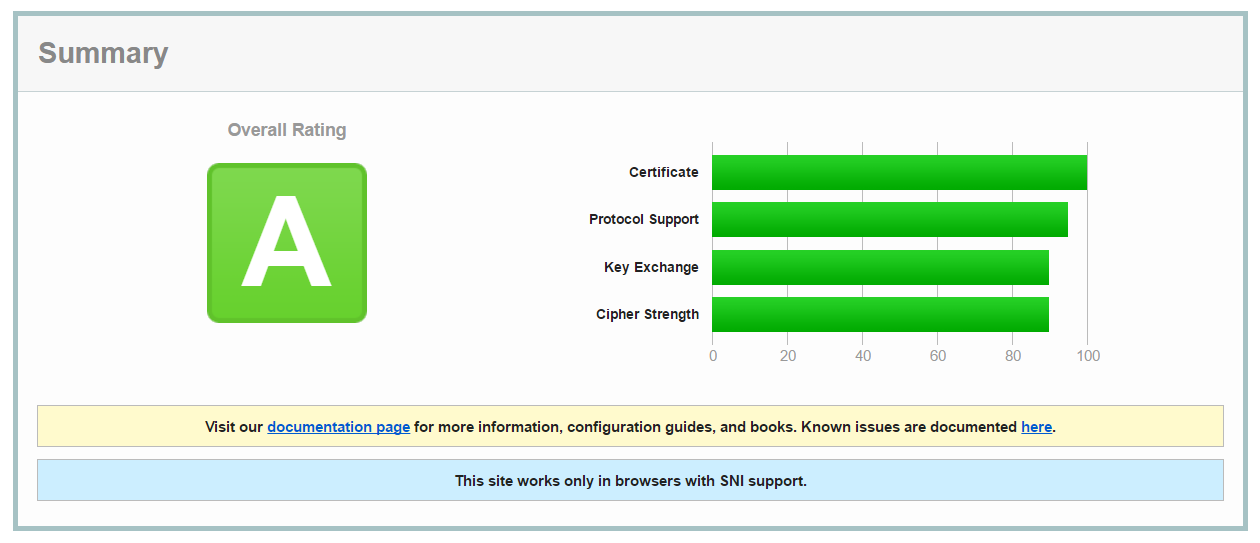
You can test your website on https://www.ssllabs.com/ssltest/ before and after you have run the script.
Also very important, always make a backup before changing, in this case you can make a backup of the following Registry Keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL
The Script
The script is located at: https://www.hass.de/content/setup-your-iis-ssl-perfect-forward-secrecy-and-tls-12b (All credit of this great script goes to Alexander Hass).
Another good place to go for Scanning you IIS and website for Security overview is: https://asafaweb.com/